Financial services regulations demand more than secure storage. They require comprehensive audit trails proving who accessed what data, when modifications occurred, and how information moved between systems. For FinTech companies building on Supabase, maintaining compliance while synchronizing data with enterprise CRMs, ERPs, and systems of record presents unique challenges.
Traditional batch synchronization obscures the audit trail. Manual exports lack timestamps. Point-to-point integrations create gaps in record sequences. Regulatory frameworks from SOC 2 to FINRA require tamper-proof, chronological records of all data events across your entire technology stack.
FinTech organizations operate under multiple overlapping regulatory frameworks. GDPR mandates transparent data processing with individual rights to access and erasure. SOC 2 requires documented controls around security, availability, and confidentiality. Financial regulations from SEC Rule 17a-4 to FINRA Rule 4511 demand unalterable records with precise timestamps.
Data synchronization introduces compliance complexity missing from single-system architectures. When customer information flows from Supabase to Salesforce CRM, compliance teams must prove data integrity throughout the transfer. When account modifications in NetSuite ERP sync back to Supabase, audit trails must reconstruct the complete sequence of changes across both platforms.
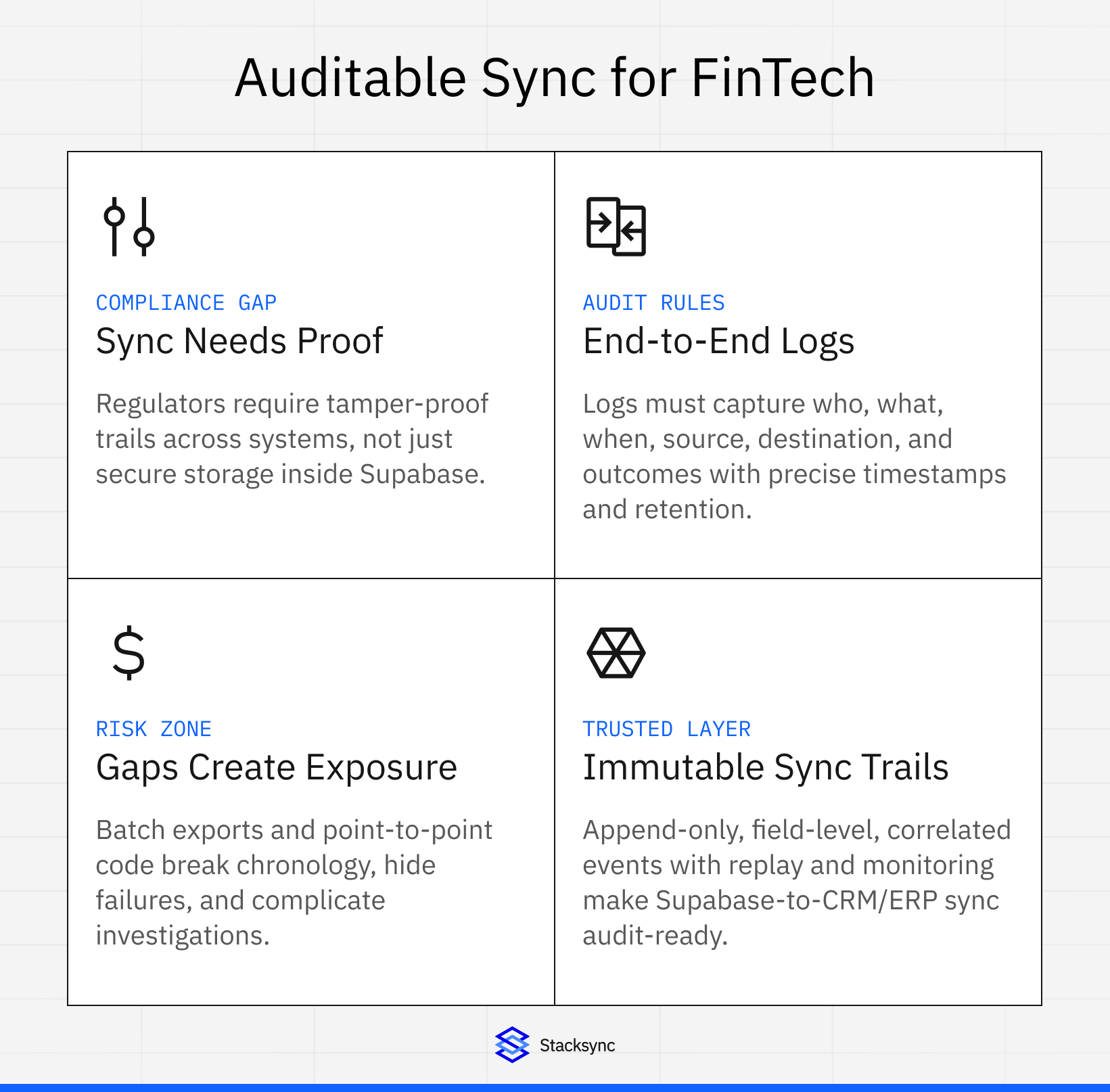
Multiple regulations converge on core audit trail requirements despite different compliance objectives. Every audit log must capture user identification linking actions to specific accounts rather than generic credentials. Precise timestamps using synchronized time sources establish event chronology. The logged event type documents whether data was created, read, updated, or deleted. Success or failure indicators show whether operations completed or encountered errors. Source and destination information identifies which system initiated the action and which received data.
FINRA's Consolidated Audit Trail requires broker-dealers to timestamp events within 50 milliseconds of NIST standard time. This precision enables reconstructing market events across distributed systems. Healthcare providers under HIPAA must log every access to protected health information including the specific user, timestamp, and data elements viewed. SOX compliance mandates maintaining detailed logs of financial data modifications with controls preventing unauthorized changes.
The challenge intensifies with bidirectional synchronization. Traditional one-way exports create linear audit trails showing data flowing from source to destination. Bidirectional sync requires coordinated logging in both directions, maintaining sequence across systems, and proving data consistency despite concurrent modifications.
Supabase provides SOC 2 Type 2 compliance for Team and Enterprise customers. Independent auditors verify controls around the Trust Services Criteria covering security, availability, processing integrity, confidentiality, and privacy. The certification demonstrates Supabase implements industry-standard practices for protecting customer data.
All customer data encrypts at rest using AES-256 encryption. Data in transit uses TLS encryption preventing interception. Sensitive information like access tokens and keys receive additional application-level encryption before database storage. These encryption layers protect data within Supabase infrastructure.
Supabase maintains HIPAA compliance through Business Associate Agreements available on Team and Enterprise plans. Organizations storing Protected Health Information sign BAAs establishing shared responsibility for HIPAA obligations. The platform provides technical safeguards including encryption, access controls, and audit logging supporting HIPAA requirements.
Row-Level Security policies leverage PostgreSQL's native RLS capabilities. Developers define SQL-based access policies determining which users access specific data rows. This granular control ensures users query only authorized information, critical for multi-tenant applications managing customer data from multiple organizations.
Authentication audit logs automatically capture all authentication events. Login attempts, password changes, multi-factor authentication events, and session activities generate log entries stored in the auth.audit_log_entries table. These logs provide visibility into who accessed the system and when.
Projects isolate in dedicated PostgreSQL instances preventing data leakage between customers. Database backups occur daily for paid plans. Point-in-Time Recovery enables restoring databases to any moment, supporting data recovery and compliance investigations requiring historical state reconstruction.
Despite strong security foundations, Supabase's native capabilities don't address audit requirements for data flowing to external systems. Authentication logs show who accessed Supabase but don't track how data moved to Salesforce, NetSuite, or other enterprise platforms. Database triggers could log some sync events but lack comprehensive visibility into the complete data lifecycle.
PostgreSQL provides robust audit capabilities through extensions like pgAudit. However, these track database operations, not API-level data synchronization with external systems. When Supabase data syncs to enterprise CRMs or ERPs, organizations need audit trails spanning both environments.
Compliance frameworks require proving data integrity end-to-end. Showing customer records exist correctly in Supabase isn't sufficient. Auditors need evidence the same data synchronized accurately to Salesforce, that modifications in either system propagated correctly, and that the complete sequence of changes maintains a verifiable chronological record.
Salesforce, NetSuite, SAP, and other enterprise platforms maintain their own audit trails. Salesforce Field History Tracking logs changes to specific fields. Setup Audit Trail records configuration modifications. Event Monitoring provides detailed logs of user actions, API calls, and system events.
NetSuite maintains audit trails for transactions, record modifications, and user activities. The platform logs who created or modified records, what fields changed, and when actions occurred. These audit capabilities support financial compliance for organizations managing accounting, inventory, and order management in NetSuite.
The challenge emerges when data synchronizes between Supabase and these platforms. Each system logs events within its boundary. Salesforce knows a contact record changed at 14:32:15. Supabase knows the same customer record updated at 14:32:17. Neither system alone proves the change in one triggered the update in the other or that data remained consistent throughout the transfer.
Point-to-point integrations create audit gaps. Custom code pulling data from Supabase and pushing to Salesforce might log operations in application logs. These logs live separately from both platforms' native audit systems. Reconstructing a compliance event requires correlating three separate log sources with different timestamps, formats, and retention policies.
Batch exports lack granular audit trails. Nightly CSV exports from Supabase to NetSuite show which records existed at export time. They don't show individual record modifications, field-level changes, or the sequence of updates throughout the day. Financial auditors requiring precise transaction sequences find batch audit trails insufficient.
Manual processes introduce unauditable steps. When engineers export data, transform it, and import to destination systems, the manual manipulation escapes automated logging. Compliance frameworks prohibit unaudited data handling for sensitive information. Organizations need continuous, automated audit trails eliminating manual gaps.
Stacksync addresses these synchronization audit gaps through purpose-built compliance features. The platform maintains comprehensive logs of every sync operation across the complete bidirectional flow between Supabase and enterprise systems.
Every synchronization event generates detailed log entries. When a Supabase database record changes, Stacksync logs detect the modification, capture the changed fields and values, record the source timestamp, identify the triggering user or process, and document the target system for propagation. When the change syncs to Salesforce, additional log entries record the destination write operation, resulting Salesforce record ID, success or failure status, and any field transformation applied.
This bidirectional logging creates complete audit trails spanning both systems. Compliance teams reconstruct exactly how customer data moved from Supabase to Salesforce, when each step occurred, what transformations applied, and whether operations succeeded. The logs provide evidence satisfying SOC 2 requirements for system processing integrity.
Event logs include unique identifiers linking related operations. A single customer update in Supabase might trigger multiple downstream actions. Creating a new contact, updating related opportunities, and notifying other services generate separate events. Stacksync's correlation IDs link these related events enabling auditors to trace the complete chain of operations from initial trigger through final completion.
Stacksync implements append-only logging preventing modification of historical records. Once written, log entries become immutable. Even system administrators cannot alter or delete past events. This tamper-proof design ensures audit logs provide trustworthy evidence for compliance investigations.
Cryptographic integrity verification protects against tampering. Each log entry includes a hash derived from the event data. Sequential entries link through cryptographic chains. Modifying any single entry breaks the chain, immediately revealing tampering attempts. This design provides mathematical proof of log integrity without requiring blockchain infrastructure.
Log retention policies align with regulatory requirements. SOC 2 implementations typically require 7-day log retention for operational monitoring. Enterprise plans provide 30-day retention. Financial services organizations requiring multi-year retention for SEC or FINRA compliance configure extended retention in secure storage.
Time synchronization across all Stacksync components ensures accurate event sequencing. The platform synchronizes with authoritative time sources maintaining accuracy within milliseconds. This precision enables compliance with regulations like FINRA CAT requiring 50-millisecond timestamp accuracy for securities transactions.
Stacksync logs capture granular field-level details, not just record-level modifications. When a customer's email address changes in Supabase, the audit trail shows the previous value, new value, field name, modification timestamp, and user who triggered the change. This granularity supports compliance frameworks requiring precise documentation of personal data modifications under GDPR.
Field mapping transformations receive dedicated logging. When synchronizing Supabase's customer_email field to Salesforce's Email field, Stacksync logs record the source field name, destination field name, transformation rules applied, and resulting values. Auditors trace how data transforms during synchronization proving accuracy and consistency.
Conflict resolution decisions appear in audit logs. When both Supabase and Salesforce modify the same customer record simultaneously, Stacksync's conflict resolution logic determines which change prevails. The audit trail documents both conflicting values, the resolution strategy applied, the winning value selected, and the timestamp of the decision. This transparency proves data integrity despite concurrent modifications.
Organizations implementing compliant synchronization between Supabase and enterprise systems follow structured patterns balancing operational requirements with audit obligations.
FinTech applications often use Supabase for operational data and Salesforce for customer relationship management. Customer records, transactions, and account information live in Supabase supporting real-time application features. Sales teams work in Salesforce accessing customer information, tracking opportunities, and managing relationships.
Stacksync maintains bidirectional synchronization ensuring both systems stay current. When new customers sign up in the Supabase-powered application, Stacksync detects the database insert, extracts relevant fields for Salesforce, maps customer data to contact and account objects, writes to Salesforce maintaining field relationships, and logs the complete operation sequence.
Sales teams updating contact information in Salesforce trigger reverse synchronization. Stacksync detects Salesforce modifications, validates changes against business rules, maps updated fields back to Supabase schema, writes to Supabase PostgreSQL database, and documents the full audit trail. Application users immediately see sales team updates through Supabase real-time features.
The audit trail spans both platforms proving data consistency. Compliance teams query Stacksync logs showing every customer record creation, modification, and synchronization event. Combined with Supabase authentication logs and Salesforce Event Monitoring, organizations maintain comprehensive audit trails satisfying SOC 2, GDPR, and financial regulations.
Payment processors, lenders, and financial platforms synchronize transaction data between Supabase operational databases and NetSuite or SAP financial systems. Transaction records, payment events, and account balances require precise synchronization supporting financial reporting and compliance.
Stacksync provides field-level accuracy critical for financial data. When payment transactions record in Supabase, synchronization to NetSuite captures transaction amount with full precision, payment method and processor details, timestamp accurate to milliseconds, customer account identifiers, and any fees or adjustments. The audit trail proves every financial record synchronized accurately without data loss or corruption.
Reconciliation reports leverage synchronized audit trails. Finance teams comparing Supabase transaction logs against NetSuite general ledger use Stacksync audit logs to verify every transaction synchronized correctly. Discrepancies trigger investigations using detailed field-level logs showing exactly what data moved between systems.
Year-end audits and regulatory examinations rely on complete audit trails. External auditors access Stacksync logs proving financial data integrity across systems. The tamper-proof logs provide evidence that transaction records remained accurate throughout synchronization satisfying SOX section 404 requirements for internal controls.
Compliance reporting often requires aggregating data from operational systems into analytics platforms. Supabase operational data flows to Snowflake, BigQuery, or Databricks for regulatory reporting, risk analysis, and compliance monitoring.
Stacksync synchronizes Supabase tables to data warehouse destinations maintaining full audit trails. Customer data, transaction histories, and operational metrics sync continuously providing up-to-date analytics substrates. Compliance teams run reports against current data rather than waiting for nightly batch processes.
The audit trail documents data lineage from source to analytics. Compliance officers investigating customer complaints trace data through the complete pipeline. Stacksync logs prove customer record X in Supabase synchronized to warehouse row Y at specific timestamp. Combined with transformation logic documentation, organizations demonstrate data accuracy for compliance investigations.
Data retention policies coordinate across systems. GDPR right-to-erasure requests require deleting customer data from all systems including analytics warehouses. Stacksync audit trails identify every system receiving customer data enabling complete erasure. Logs prove deletion occurred across all platforms satisfying GDPR Article 17 requirements.
Regulatory audits demand presenting evidence proving controls operate effectively. Stacksync audit trails provide multiple evidence types supporting compliance examinations.
Stacksync generates reports aligned with common audit requirements. SOC 2 examinations require demonstrating access controls, monitoring capabilities, and incident response procedures. Stacksync reports show user access patterns to synchronization logs, sync error rates and resolution procedures, and data processing integrity across synchronized systems.
GDPR compliance requires documenting personal data flows. Stacksync mapping reports show which Supabase fields containing personal data sync to which Salesforce or NetSuite fields. Processing activity records document data transfer purposes, legal bases for processing, and retention periods. These reports support GDPR Article 30 requirements for processing records.
Financial services regulators examining transaction audit trails access reports showing transaction synchronization completeness, timestamp accuracy across systems, field-level accuracy for monetary amounts, and error rates with remediation evidence. These reports demonstrate controls preventing transaction data corruption during synchronization.
Compliance teams export audit logs in standard formats for analysis and evidence presentation. CSV exports provide tabular data for spreadsheet analysis. JSON exports enable programmatic processing and integration with compliance management platforms. SIEM integrations send logs to security information and event management systems for correlation with broader security monitoring.
Log exports include complete event details with no summarization or aggregation obscuring evidence. Every field change, every synchronization operation, and every error appears in exported logs. External auditors independently verify log completeness and accuracy.
Encrypted log exports protect sensitive information during transfer to auditors or regulators. Logs containing customer personal data or financial transaction details encrypt with auditor-provided public keys. Only intended recipients decrypt exported logs maintaining confidentiality throughout the audit process.
Proactive compliance monitoring prevents issues before audits. Stacksync alerting capabilities notify compliance teams of synchronization anomalies. Unexpected sync errors exceeding thresholds, unusual volumes of data modifications, authentication failures suggesting security issues, and extended sync delays violating service levels trigger immediate alerts.
Integration with compliance management platforms enables automated evidence collection. Vanta, Drata, and similar GRC platforms query Stacksync APIs collecting audit log evidence continuously. Rather than scrambling during annual SOC 2 audits, organizations maintain current compliance posture with Stacksync logs automatically feeding evidence repositories.
Dashboard visualizations show compliance metrics in real-time. Sync success rates, error resolution times, and data consistency metrics appear on compliance dashboards. Executives and board members monitor compliance health without reviewing raw audit logs.
Audit trail integrity requires protecting the logs themselves from unauthorized access or modification.
Stacksync implements role-based access control for audit log access. Compliance officers receive read-only permissions viewing logs without modification capabilities. Security teams access detailed error logs for incident response. Finance teams access transaction synchronization logs for reconciliation. Each role sees only relevant information maintaining least-privilege principles.
Multi-factor authentication protects audit log access. Viewing sensitive synchronization logs requires both password authentication and MFA verification. SSO integration through SAML or OAuth delegates authentication to enterprise identity providers maintaining consistent access policies across all platforms.
Audit logs for audit log access create meta-trails proving appropriate access patterns. When compliance officers query synchronization logs during investigations, those queries generate their own audit entries. Security teams reviewing who accessed audit logs maintain oversight preventing unauthorized log review.
Audit logs encrypt at rest using AES-256 encryption matching or exceeding regulatory requirements. Encryption keys rotate regularly following security best practices. Cloud-based storage leverages provider encryption capabilities with customer-managed keys providing additional control.
Transmission of logs between Stacksync infrastructure and storage uses TLS encryption preventing interception. API access to audit logs requires encrypted connections. Log exports download over HTTPS ensuring confidentiality during transfer.
Regional data residency controls support data sovereignty requirements. European customers configuring EU data processing ensure audit logs remain within EU regions satisfying GDPR Article 44 restrictions on international transfers. Financial institutions with specific jurisdictional requirements configure appropriate processing regions.
Configurable retention policies align with organizational compliance requirements and storage optimization. Development teams might retain 7 days of logs for troubleshooting. Financial institutions retain transaction logs for 7 years satisfying SEC requirements. Healthcare organizations retain patient data access logs for 6 years under HIPAA.
Automated archival moves aged logs to cost-effective long-term storage. Recent logs reside in high-performance storage supporting real-time queries. Logs older than 90 days automatically archive to object storage reducing costs while maintaining accessibility. Compliance teams retrieve archived logs when needed for investigations or audits.
Secure deletion procedures ensure logs delete completely when retention periods expire. Cryptographic erasure of encryption keys renders archived logs unrecoverable. This secure deletion satisfies GDPR requirements for data minimization and storage limitation while maintaining logs during necessary retention periods.
Organizations preparing for SOC 2, GDPR, or financial services audits leverage Stacksync audit trails as primary evidence sources.
Auditors require understanding how synchronization works before evaluating controls. Organizations provide data flow diagrams showing how information moves between Supabase and enterprise systems through Stacksync. System architecture documentation explains security controls, encryption methods, and access restrictions. Data classification guides identify which synchronized fields contain personal data, financial information, or other sensitive categories requiring special handling.
Synchronization policies document business rules for conflict resolution, error handling, and data validation. When Supabase and Salesforce contain conflicting customer information, documented policies explain which system prevails. Auditors verify actual Stacksync configurations match documented policies through log review.
Incident response procedures explain how teams handle synchronization failures. Documentation covers error detection through monitoring and alerting, incident classification and priority assignment, remediation procedures for different failure types, and verification of data consistency after remediation. Stacksync audit logs provide evidence these procedures execute correctly when incidents occur.
SOC 2 Type 2 audits examine controls over minimum 3-month periods. Compliance teams collect Stacksync audit logs spanning the audit period demonstrating consistent control operation. Logs show access controls prevented unauthorized modifications, monitoring detected and alerted errors promptly, and incident response procedures resolved issues appropriately.
Sample selection methodology determines which log entries auditors examine in detail. For high-volume synchronization environments generating millions of log entries monthly, auditors select statistical samples. Organizations explain sampling methodology ensuring representative coverage of different sync types, time periods, and operational conditions.
Evidence packages bundle logs with supporting documentation. For each audited control, packages include relevant audit log excerpts, screenshots showing dashboard metrics, incident reports with resolution details, and change management records for configuration updates. Well-organized evidence packages accelerate audit completion.
External auditors often require direct log access for independent verification. Organizations provision read-only auditor accounts with appropriate access scopes. Accounts activate only during audit periods and deactivate afterward maintaining least-privilege principles.
Screen sharing sessions enable auditors to see real-time dashboards and query capabilities. Compliance teams demonstrate log search functionality, filter by date ranges and event types, and export logs for offline analysis. These demonstrations prove log completeness and accessibility without requiring auditors to learn Stacksync interfaces.
Attestation reports from Stacksync itself support nested service organization requirements. As a service provider managing synchronization infrastructure, Stacksync maintains its own SOC 2 compliance. Organizations reference Stacksync's SOC 2 report in their own compliance documentation showing appropriate vendor due diligence.
Compliance frameworks provide specific guidance on audit trail requirements. Organizations align Stacksync implementations with these standards.
Common Criteria 2.0 requires organizations have a system description identifying infrastructure and software supporting objectives. Documentation includes describing Stacksync's role in the technology environment, mapping synchronized data flows, and explaining how audit trails support control objectives.
Security criterion CC6.2 addresses monitoring of control operations. Organizations demonstrate monitoring by configuring Stacksync alerts for sync failures, reviewing error logs for anomalies, and responding to security-relevant events. Audit logs prove monitoring controls operate effectively throughout the audit period.
Confidentiality criterion C1.1 requires controls limiting access to confidential information. Stacksync access controls, encryption, and audit trails demonstrate how organizations prevent unauthorized access to synchronized personal data or financial information.
Article 5(1)(a) requires processing personal data lawfully, fairly, and transparently. Stacksync audit trails support transparency by documenting exactly what processing occurred. Individuals exercising GDPR rights access audit logs showing how their data synchronized across systems.
Article 5(1)(f) mandates appropriate security for personal data. Comprehensive audit trails detecting unauthorized access or data modifications satisfy security requirements. Logs showing encryption, access controls, and incident detection demonstrate appropriate technical measures.
Article 30 requires maintaining records of processing activities. Stacksync audit logs combined with synchronization configuration documentation satisfy this requirement. Records show which personal data fields synchronized, processing purposes, legal bases, and retention periods.
SEC Rule 17a-4 requires broker-dealers preserve electronic records in non-rewritable, non-erasable format. Stacksync's immutable audit logs satisfy WORM storage requirements. Transaction synchronization logs between Supabase and financial systems provide required audit trails.
FINRA Rule 4511 mandates books and records for member firms. Synchronization logs showing customer account information, transaction details, and communications constitute required records. Organizations configure appropriate retention periods matching FINRA requirements typically spanning 3-6 years.
Bank Secrecy Act requirements for anti-money laundering compliance include maintaining transaction records. Stacksync logs documenting payment transaction synchronization between Supabase and core banking systems support AML compliance programs and regulatory examinations.
Organizations building compliant FinTech platforms on Supabase establish synchronization compliance from inception rather than retrofitting later.
Design data architectures with compliance as primary requirement alongside performance and functionality. Map personal data fields requiring GDPR protections, identify financial data elements needing SOX controls, and document sensitive information categories determining security requirements. This classification drives synchronization configuration ensuring appropriate handling.
Implement synchronization with compliance controls enabled from day one. Rather than treating audit logging as optional feature added later, enable comprehensive event logging, configure alerts for compliance-relevant conditions, and establish monitoring procedures before production launch. Organizations avoid compliance gaps from incomplete audit trails.
Maintain documentation continuously as systems evolve. When adding new Supabase tables to synchronization scope, update data flow diagrams, document field mappings and transformations, and explain compliance controls for new data categories. Current documentation supports both ongoing compliance and audit preparedness.
FinTech compliance transcends checkbox exercises. Comprehensive, tamper-proof audit trails demonstrating data integrity across Supabase and enterprise systems build customer trust, satisfy regulatory obligations, and enable confident scaling. Stacksync provides the synchronization audit capabilities turning compliance requirements into operational advantages through transparency and accountability.
Ready to implement compliant bidirectional sync between Supabase and your enterprise systems? Stacksync delivers production-grade synchronization with comprehensive audit trails, SOC 2 compliance, and enterprise security. Schedule a demo to discuss your specific regulatory requirements and discover how Stacksync transforms compliance from burden to competitive advantage.